Technology for the protection of confidential data in traditional data carriers on paper and plastic based on digital holography
M.V. Smirnov, Saint-Petrsburg, Russua.
smirnoff04@mail.ru
Russian
 |
At the same time, the main obstacle to digital hacking is the analog representation of the hidden data in the photo carrier. Visually observed documents and photographs, in any case, are analog regardless of whether the picture was taken with a digital camera or film. The last statement is also true for viewing photographs on a monitor screen.
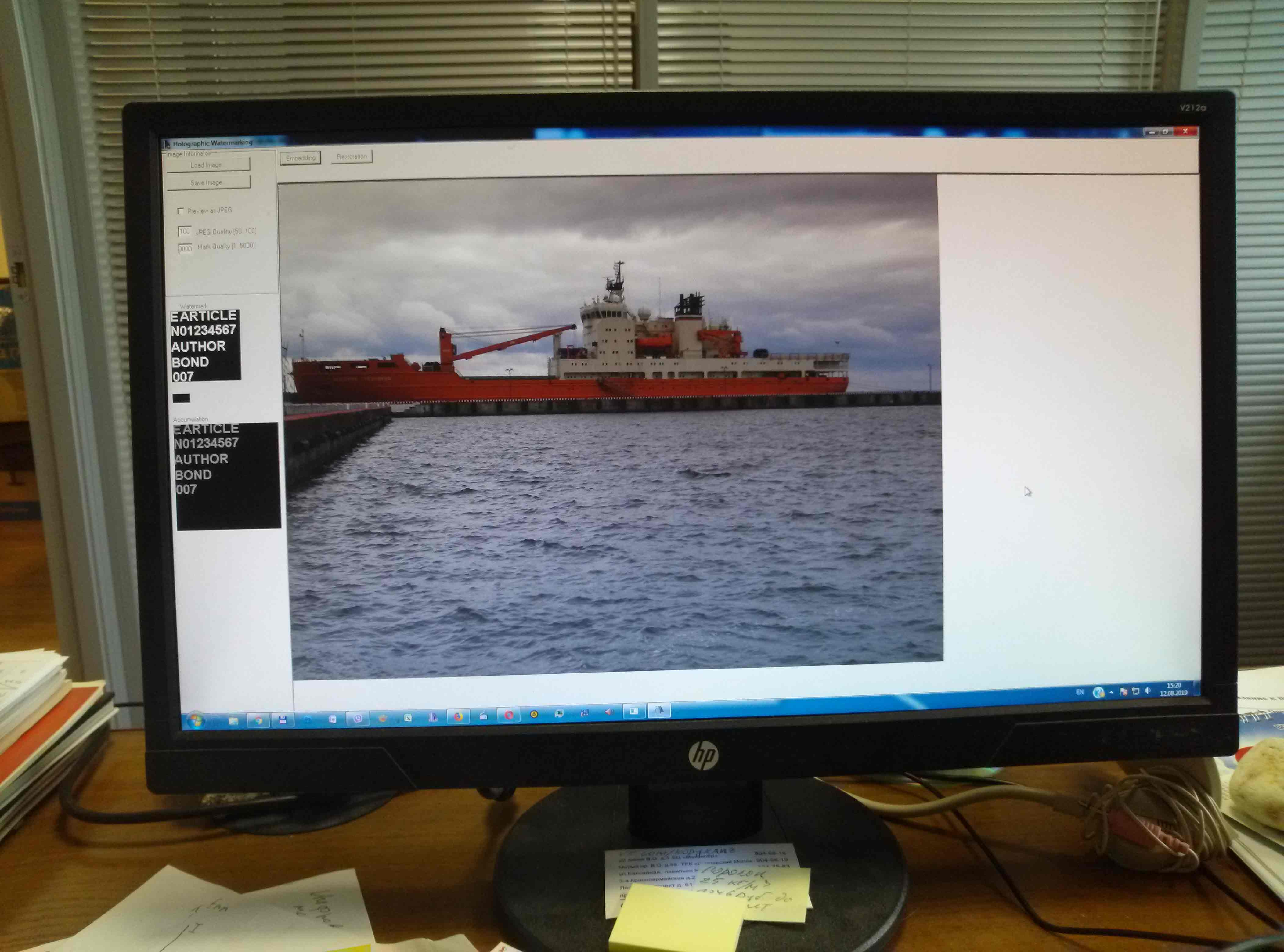
SOLUTION. The presented Holographic WaterMark (HWM) technology is designed to conceal and protect confidential data in traditional storage media using digital holography techniques to provide comprehensive information security.
HWM technology enables the implementation and storage of hidden data in photographic media on paper or plastic basis. Unlike well-known technologies, the identification object and the security tool form a single conditionally dependent object. A combination of the steganographic concealment approach and cryptographic data encryption is provided. The decision on the ownership of the document is based on the visual perception of the recovered hidden data.
The application of the technology is not associated with a change in existing technologies for the production of documents and plastic cards. HWM technology is based on the use of standard office equipment.
SHORT DESCRIPTION. The work is devoted to the creation of technology and software for analog-to-digital data hiding and protection in traditional storage media, as well as electronic documents to ensure integrated information security. The module package is implemented in the C ++ programming language in the environment of Borland Builder.
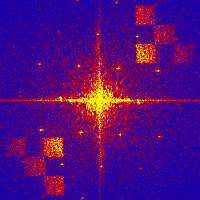
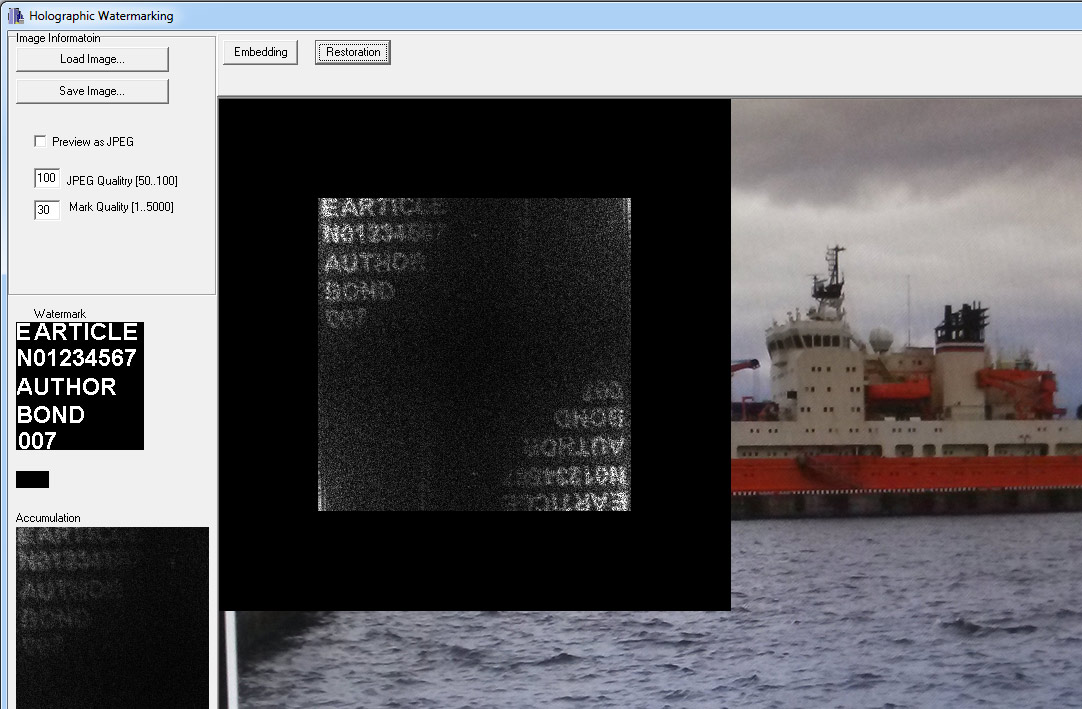
Methodologically, HWM technology and software are two independent processes for the synthesis and restoration of digital Fourier holograms. The first process is intended for the synthesis of digital Fourier holograms of hidden data (identifiers, labels), and their integration into analog data carriers. The second process is the reverse and consists in restoring a hologram of hidden data. A hidden data detection event is used to decide on the authenticity of a document or the rights of the owner. The holographic approach and theoretical justification are presented in [1], which established that embedding hidden data in the image spectrum equivalent to embedding the Fourier hologram of this data in the image.
HOW IT WORKS.
Example I. Embedding hidden identities in printed matter.
In the example, the initial data for protection is a digital magazine layout made programmatically for subsequent printing on a printer. This procedure, in accordance with the elements of the conversion path, is called «print-scan».
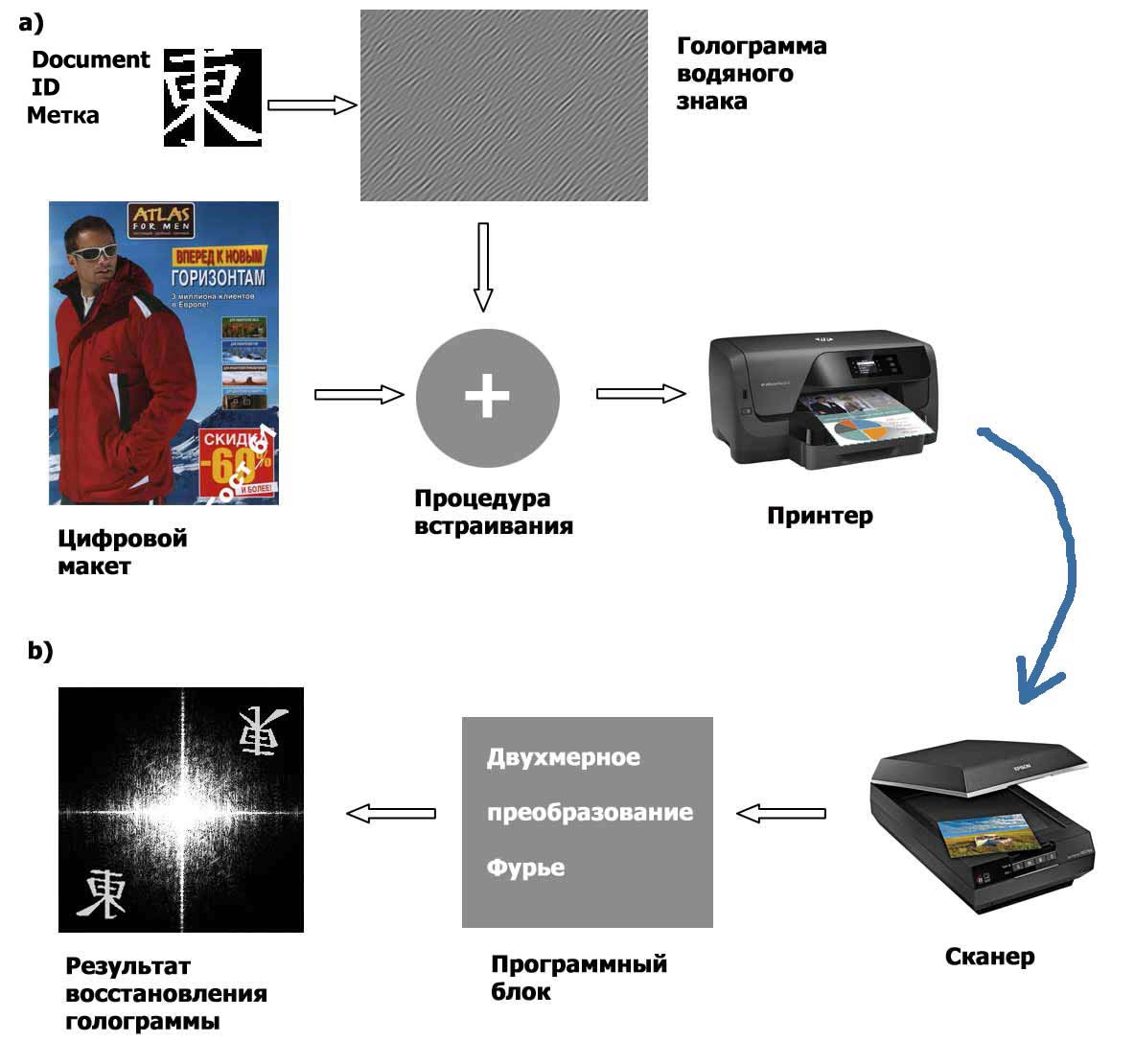
|
1) Original image for printing (digital layout)

|
A copy of the original Atlas for Men magazine cover text is presented.
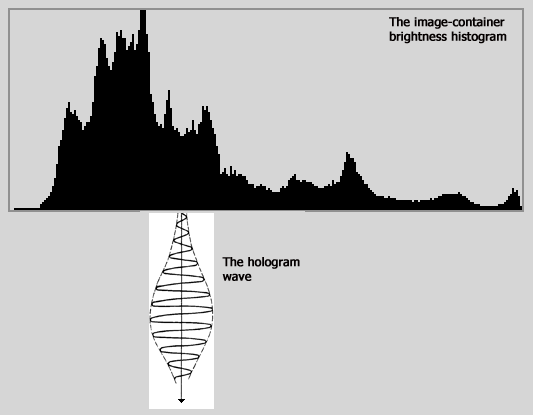
1.2) Luminance histogram of the original container image
|
1.3) Image container after embedding the identification code

|

|
Fig. 1.4. Enlarged fragment (300%) of the container image with a built-in identifier after printing and subsequent scanning (“print-scan” process)
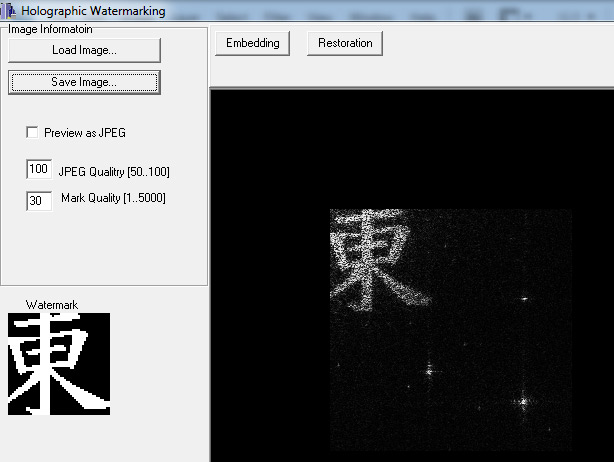
1.4) Result of restoring a hologram of a hidden identification code
|
Example II. Embed Holograms of Hidden Identifiers in High-Quality Art Reproductions

|
.jpg)
|
Пример III. Embedding holograms of hidden identifiers in images on a monitor screen
|
|
Пример IV. Embedding holograms of hidden identifiers in plastic images

|

|

|
Example V. Protection of documents in DOC, PDF, HTML and other electronic documents with hidden identifiers

|

|
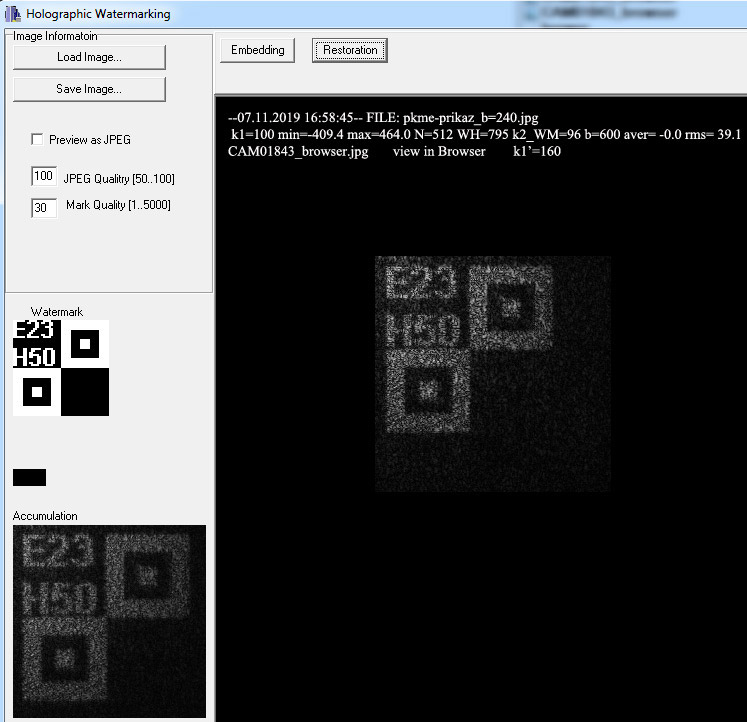
|
Example VI. Transmission of cipherograms in container-images
The combination of encryption (cryptography) and data hiding in container images provides high security for the transmission of confidential information over open communication channels. Encryption is performed by methods of permutation of elements of a binary image of a text message.

|

|

|
On the right is an image and a histogram with a built-in hologram of a text message.
The open communication channel receives an image with a built-in hologram (the picture on the right in Fig.6.2.). On the recipient's side, the hologram is detected (the picture on the left in Fig.6.3.).

|

|
On the right is the result of restoring a hologram of a text message.
COMPETITION.
a) Manufacturers of protective optical holograms that are applied over documents. Conceptually, this technology differs little from applying a conventional printing stamp on top of a document. The technology does not have a conditional dependence according to the scheme "security element - protected document". Replacing a document with a protective element applied over it will not indicate falsification.
b) Manufacturers of intelligent micro-chips that can be implanted, for example, into credit cards. The cost of such micro-chips exceeds the cost of embedded hidden data in plastic by HWM technology by 2-3 orders of magnitude. There is a high probability of hacking.
MARKET.
a). Provision of printing services for paper and photographic materials with hidden identification data
b) Provision of services for identification of the owner of printing products
c) Gos. orders for the production of certificates, diplomas, certificates, passports, documents on plastic with embedded hidden data
d) HWM Software Product License Selling
HWM Software Partners the production of modern household digital equipment:
- digital cameras
- scanners and printers
- digital signal processors
- printing manufacturers
CONTACTS. LEGAL STATUS.
Michael Smirnov
E-mail: smirnoff04@mail.ru
http://smirnov.spb.su
Saint-Petersburg, Russia
[1] Голографический подход к встраиванию скрытых водяных знаков в фотографии
[2] M.V. Smirnov. Holographic approach to embedding hidden watermarks in a photographic image - Journal of Optical Technology Vol. 72, Issue 6, pp. 464-468 (2005)